So if you don't like that blue, or perhaps you are using that same color for some text and you want invisibles to stand out you can easily change them in Pages.So you can find this kind of functionality on almost all word processing apps. 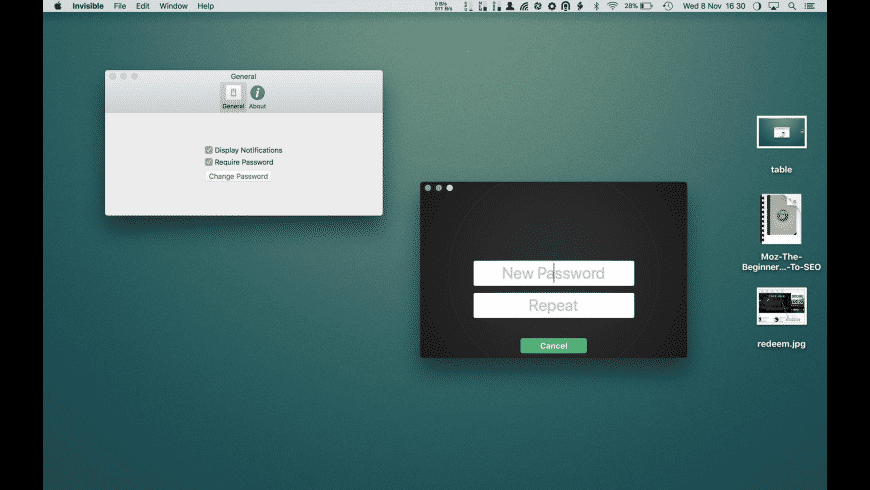 It is easy to see that with invisibles turned on.Now you've got the ability to control the color of the invisibles right here in Preferences for Pages under General and there is a color control for that.
It is easy to see that with invisibles turned on.Now you've got the ability to control the color of the invisibles right here in Preferences for Pages under General and there is a color control for that.
- Is it literally not using the flash drive at all after bootup, meaning the size of that drive cannot matter at all as long as I can install the OS on it and boot it up? In the Download Center there is a NiceHash OS User Guide pdf download. In the guide under prerequisites it says: - Your mining rig needs at least 2GB of RAM.
- The 1st and best native Mac OS X Bitcoin/Litecoin mining app with the most features, inc. Cgminer, bfgminer and cpuminer as well as API output monitoring for local or networked miners. Mine Bitcoin and Litecoin on Mac OS X - for free.
- Cgminer is a combined FPGA and ASIC bitcoin miner written in C, cross platform for Windows, Linux, and Mac OS X, with stratum support, remote interface capabilities, support for multiple simultaneous mining devices, and advanced caching and detection algorithms that maximize cryptocoin mining efficiency.
- Data Mining for Mac. Data Mining for Mac. Free Custom Solutions of Maryland Mac OS X 10.10/10.6/10.7/10.8/10.9 Version 2.5.0 Full Specs. Download Now Secure Download. Publisher's Description.
OS X 10.7 or later Any Mac with 64-bit CPU Minimum screen resolution of 1280 x 768 For Excel support, Excel versions 2011 or 2008 74.5 MB Pricing and Availability: Insights 2.0.3 Touch Edition, regularly $80.00 (USD), will be available free for one day only, September 18, 2013, directly from the KnowledgeMiner Software website.

Honeypot Network Forensics
NCC Group recently released a 500 MB PCAP file containing three months of honeypot web traffic data related to the F5 remote code execution vulnerability CVE-2020-5902. In a blog post the NCC Group say that their objective is 'to enable all threat intelligence researchers to gain further understanding and contribute back to the community'.
The data in NCC's 500 MB capture file 'f5-honeypot-release.pcap' ranges from July 7 up until September 28 and contains traffic from over 4000 unique client IP addresses. The packets are captured after having passed through a proxy, which is why all clients have IP '123.45.67.89' and the server is always displayed as '127.0.0.1'. This makes it difficult to split or filter the traffic based on the client IP address. Many HTTP headers have also been masked in the capture file, but the IP portion of the 'X-Forwarded-For' header is still intact. You can therefore track clients throughout the capture file by filtering on the 'X-Forwarded-For' header, which contains the originating IP address of the client connecting to the proxy. 3u tools for mac. As an example, you can use the following tshark command in order to count the exact number of unique clients in the released PCAP file:
4310
Tracking a Single Actor
I decided to focus on one of the over 4000 clients in NCC's capture file in this blog post. The selected actor is primarily originating from the IP address 45.12.206.76, which is a VPN egress point according to Scamalytics. I can therefore not be certain that only a single actor is caught with this filter, but the consistent behavior across the various sessions indicates so.
Some characteristic traits of the actor's traffic is:
- Web browser User-Agent :
Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:55.0) Gecko/20100101 Firefox/55.0 - Uses VPN from Think Huge Ltd, IP range announced by AS9009 'M247 LTd'
- Active between 21:55 and 05:08 UTC on weekdays as well as weekends
I started by opening the full 500 MB PCAP file from NCC Group in CapLoader. Then I narrowed the dataset down to a single client IP address by clicking
After pressing 'Find All Matching Flows' I got a much smaller dataset (144 kB) containing only the sessions for this specific IP address.
July 7 22:16 UTC - First Contact
The actor with IP address '45.12.206.76' can be observed attacking the vulnerable F5 device on July 7 at 22:16 UTC. The attack started with an attempt at exploiting the authentication bypass vulnerability in CVE-2020-5902.
Image: CapLoader Flow Transcript of the authentication bypass attack.The attacker wrote the following content to '/tmp/.X11.1' by sending an HTTP POST to 'fileSave.jsp':
The '/tmui/login.jsp' page can be accessed without authentication, so no credentials are needed for this request. But as explained in Orange Tsai's BlackHat 2018 talk 'Breaking Parser Logic!' the TMUI Tomcat service will interpret
I didn't find any attempt to execute the bash script in the '/tmp/.X11.1' file though.
July 9 04:49 UTC - Same Actor, New IP
The same actor came back again on July 9, but this time from the IP address '185.160.24.70'. The actions carried out are pretty much a reiteration of the previous attempts, i.e. writing
July 18 21:55 UTC - Java Deserialization Attack
More than a week later there is activity from the 45.12.206.76 IP address again. But this time the attacker has changed approach to instead inject a serialized piece of Java code by posting it to '/hsqldb;' This is an attempt at triggering the deserialization vulnerability in CVE-2020–5902.
As you've probably noticed the argument provided to the
Base64 decoding the data reveals the following command sent to the TMOS Shell (tmsh):
The HTTP response contains a string saying 'General error java.lang.IllegalArgumentException: argument type mismatch', which could indicate that the exploit failed. However that is probably just a side effect of the exploit, so the injected bash command might still have executed. Nevertheless the attacker POST'ed the exact same exploit three more times, getting the same IllegalArgumentException error message each time.
The attacker came back with a slightly modified payload for the deserialization attack 20 minutes later. The new payload executed this tmsh command instead:
July 19 02:54 UTC - Web Shell
Five hours after the first deserialization attack the actor came back, this time with a call to F5's 'iControl REST API' at URI '/mgmt/tm/util/bash'.

It looks like a bash command was supplied in the JSON data. The documentation for the iControl REST API confirms that this is a built in feature, not a bug or vulnerability:
The utilCmdArgs name is used to provide the command line arguments for the Advanced Shell (bash) utility. The -c option in bash is used to process any system commands [..]
However, this type of request can only be carried out by an authenticated user. The HTTP request used basic auth with 'c25tcGQ6QWJDZDAwN3hzdzI=' as credential, which decodes into 'snmpd:AbCd007xsw2'. You probably recognize this credential from the deserialization attack, where the command 'create auth user snmpd password AbCd007xsw2' was issued. The password in the basic auth header can also be observed in NetworkMiner's 'Credentials' tab.
NetworkMiner can also be used to list all all occurrences of the 'utilCmdArgs' parameter.
Image: Parameters values for 'utilCmdArgs' in PCAP data filtered onNetworkMiner shows us that the 'cat /etc/hosts' command was issued four times. We can see that the command executed successfully, because the HTTP response comes back with a JSON formatted result containing the following output from the cat command:
#The list of 'utilCmdArgs' parameters from NetworkMiner also reveals that the attacker sent the following long sequence of commands to the iControl 'Advanced Shell' utility:
# THIS IS AN AUTO-GENERATED FILE - DO NOT EDIT!!!
#
# Use the tmsh shell utility to make changes to the system configuration.
# For more information, see tmsh -a help sys global-settings.
127.0.0.1 localhost.localdomain localhost bigip1.localhost.localdomain
127.2.0.1 sccp aom AOM
127.2.0.2 bigip1.localhost.localdomain
127.1.1.255 tmm-bcast
127.1.1.253 tmm-shared
127.1.1.254 tmm
127.1.1.1 tmm0
127.1.1.2 tmm1
10.164.0.2 bigip1.localhost.localdomain
220.64.53.10 f5update.ddns.net
You probably recognize this command sequence, which was previously posted to '/tmp/.X11.1' on July 7 and 9 by attempting to exploit the authentication bypass vulnerability in CVE-2020-5902. However, this time the output from the command comes back in the HTTP response in form of a 16 kB JSON blob.
Image: CapLoader Transcript of utilCmdArgs request and reponse The PCAP file from NCC Group unfortunately only contain the first 8 kB of the full 16 kB JSON data returned from the server. It looks as if the data was cut of just before the contents of
Other Attacks with Similar Password Scheme
This blog post has outlined how an attacker created a user account called 'snmpd' on NCC Group's F5 honeypot. The password for this user account was set to
The first one creates a user account named 'system' with password
The IP address used in that attack (185.220.101.214) was an active Tor relay on July 7.
The other attack where a similar password was observed originated from IP address 198.13.54.223 on August 3'rd. This time the attacker attempted to authenticate to
However, as can be seen in the screenshot above, the login was not successful.
I'm not sure if this is a password scheme used by a specific actor or if it is an artifact of a common tool used by different actors.
Finally, there was also an actor coming in from IP address 185.201.9.198 who performed actions related to those described in this blog post. However, I'd like to cover that traffic in a separate blog post.
Posted by Erik Hjelmvik on Wednesday, 21 October 2020 12:35:00 (UTC/GMT)
Tags: #PCAP #CapLoader #NetworkMiner
Honeyminer makes mining and earning money simple for anyone with a computer.
nowNEW
Honeyminer gives anyone easy access to sophisticated mining software. Imagine earning meaningful passive income just by having your computer turned on, all while taking part in the blockchain revolution.
Sign up in a minute
Downloading Honeyminer takes less than a minute and only requires a valid email address.
Become an expert miner
Honeyminer’s proprietary algorithm will scan through dozens of cryptocurrencies to identify the most profitable coins to mine at any given time.
Stick with it
All mined coins will be automatically converted to Bitcoin and your balance will increase daily. You can keep it as an investment or sell it for cash anytime you want.
Earnings depend on the power of your graphics card as well as overall market conditions. Newer PCs can make anywhere from $15-$75* per GPU per month.
See the potential if you HODL based on annual bitcoin growth rates:
Miner For Mac Os X 10 11 Download Free
20%Your peace of mind is our highest priority and we take pride in the fact that we are setting the highest standard for mining security.
We use Secure Sockets Layer (SSL) and aggressive encryption to ensure that information passing through our servers is anonymous and protected.
Honeyminer offers 2-factor authentication to safeguard your account. We enforce strict password policies, smart session monitoring, and suspicious login activity monitors.
Mac Os X 10.11 Download Free
Every line of code is audited and compiled in-house by our security experts. No risk of malicious code distributed by anonymously-produced mining software.
We store virtually all of our user’s digital assets in cold storage (not connected to internet), protecting against even the most sophisticated online threats.
How do I get started with Honeyminer?
It’s super straightforward, download Honeyminer and then run the program after locating it in your downloads folder. After running it your computer will start mining, its that simple!
Retrieved 2013-07-07. Mariann Krizsan. Archived from on 2014-03-10. Original Myth III: The Wolf Age box. Games for pc mac.
How much can I earn?
It depends on the power of your computer specifically the graphics card(s). Computers built for gaming or newer PC’s bought in the last year will make the most. Older computers and laptops will be able to mine as well, however not at the same levels as newer ones. On the high end, newer computers can earn $1-3 per day per GPU. (based on today’s value of bitcoin)
Will Honeyminer harm my computer? (No)
Some antivirus software may flag Honeyminer as an unknown application. That’s because Honeyminer is brand new. Honeyminer software is written in the United States, compiled completely in-house, code-signed by DigiCert, and fully audited for security compliance.
Mac Os X Download For Windows
After Honeyminer is installed, you can turn it on and off as you please. Your computer should run perfectly normal with it on, the one exception would be if you were playing a graphics-intensive video game, you may want to pause Honeyminer as the same graphics card is used to mine.
Do I have to auto-convert profits to bitcoin?
For now, yes as we wanted to allow people easy access to their profits. We realize some of you will want the option to hold some or all of the coins you mine and we are building functionality to support that.
Can I choose what coins to mine?
Not at this point. Our first goal was to create a 'set it and forget it' app for anyone to mine the most profitable coins. There may be some of you that have a favorite coin to mine and we will be building functionality to support that. For now you can rest assured that Honeyminer will identify the best coins to mine for you.
I run a mining operation already, is Honeyminer for me?
Technically yes, as this helps any rig run on autopilot. However we realize that more experienced miners require much more detailed monitoring capabilities and we will be building that (and a bunch of other cool stuff) into Honeyminer Pro.
What’s Honeyminer’s Revenue Model?
Miner For Mac Os X 10.10
Honeyminer supports development by taking a small share of the total mining earnings generated on our network. For users with 1 GPU the fee is 8% and for 2 GPUs or more the fee is 2.5%.
